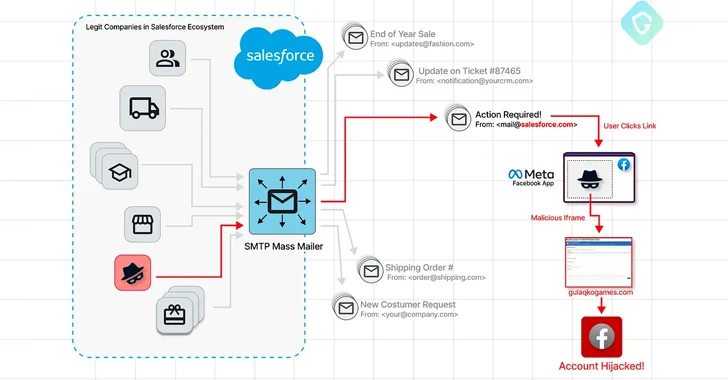
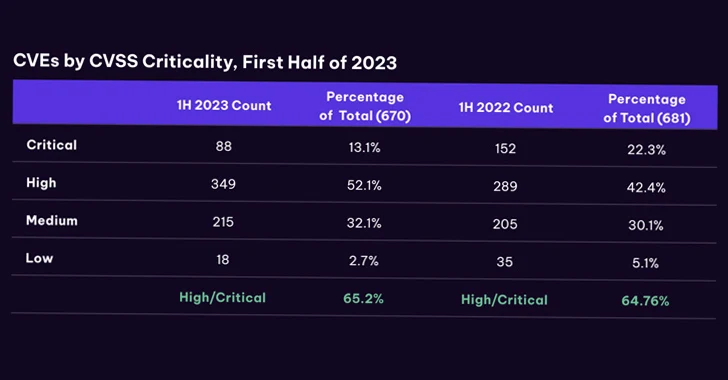
"Microsoft flags growing cybersecurity concerns for major sporting events."
Views expressed in this cybersecurity, cyber crime update are those of the reporters and correspondents. Accessed on 03 August 2023, 1301 UTC. Content provided by email subscription to "The Hacker News Daily Updates."
Source: https://mail.google.com/mail/u/0/?tab=rm&ogbl#inbox/FMfcgzGtwWCBTGNgkcnFkdQSnqhtHhpj ("The Hacker News Daily Updates").
Please click link or scroll down to read your selections. Thanks for joining us today.
Russ Roberts (https://www.hawaiicybersecurityjournal.net).
| The Hacker News Daily Updates | ||||||
 | ||||||
| ||||||
| ||||||
| ||||||
| ||||||
| ||||||
| ||||||
| ||||||
| ||||||
| ||||||
| ||||||
|